As values of various cryptocurrencies begin to rise, attackers devise new ways of generating as much cryptocurrency as they can for themselves.
According to a study published by Palo Alto Networks Unit 42 last October 2017, attackers have adapted existing malicious techniques to generate Monero, an open-source cryptocurrency much like Bitcoin but providing more emphasis on transaction privacy.
The study discovered that attackers use VBScript files and different URL-shortening services such as bit.ly to install the XMrig mining utility on unsuspecting users. Such tactics have been used for many years as a way to install malware. However, the XMrig is in itself not malware, but a legitimate open-source application to mine the Monero cryptocurrency, but the URL shorteners and VBS files make the application look like other legitimate and expected programs, installing the miner without the user’s consent.
The cryptocurrency miner then covertly runs in the background, continuously mining Monero cryptocurrency while the device is turned on.
The malware campaign is still quite young, with researchers tracing the start of such attacks four months ago; but the scale of the attacks is large, with 15 million people identified to be affected worldwide in the study. However, researchers estimate that the total number of people affected maybe double.
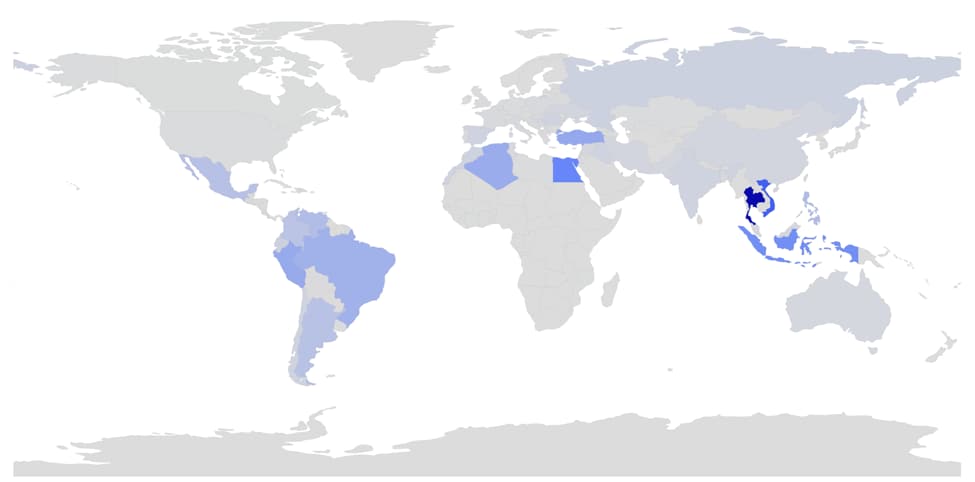
Areas of the globe with high levels of penetration include Southeast Asia, Northern Africa, and various countries in Central and South America. The top ten nations with the most number of downloads are as follows:
- Thailand – 3,545,437
- Vietnam – 1,830,065
- Egypt – 1,132,863
- Indonesia – 988,163
- Turkey – 665,058
- Peru – 646,985
- Algeria – 614,870
- Brazil – 550,053
- Philippines – 406,294
- Venezuela – 400,661
To know more about the XMrig malware attacks and other studies on cybersecurity, visit: https://researchcenter.paloaltonetworks.com
