The Kaspersky Q1 2020 DDoS attacks report has revealed the overall number of attacks grew during the first three months of the year, with a significant spike in attacks on municipal and educational sites. This can be due to the fact that DDoS actors are taking advantage of the current situation when people are locked down in their homes and are heavily reliant on digital resources.
The coronavirus pandemic, beginning in the first quarter of 2020, has caused almost all activities—be it learning, work, or leisure—to shift online. The increased demand in online resources was noted by cyberattackers, who conducted attacks on the most vital digital services or those that are growing in popularity. For instance, the US government’s Department of Health and Human Services, a group of hospitals in Paris, and servers of an online gamewere all targets of DDoS attacks in February and March.
Kaspersky’s Q1 2020 DDoS attacks report also revealed notable growth in attacks on educational resources and cities’ official websites. In Q1 2020, this number tripled compared to the same period in 2019. The share of such attacks amounted to 19% of the total number of incidents in Q1 2020.
Kaspersky experts suggest that the growth in attackers’ interest is caused by the fact that people are becoming more reliant on these online resources remaining stable and accessible during the outbreak. If they have seen conflicting messages about the virus and what preventive measures can be taken, people may look at official sources of information for more assured guidance. Many schools and universities have also shifted to online lessons.
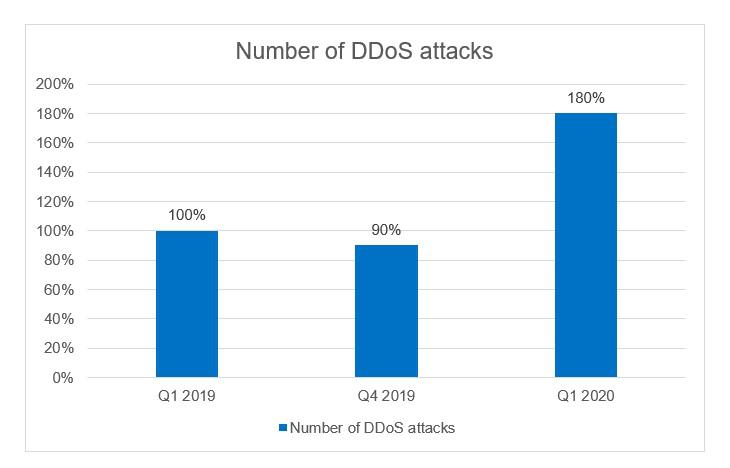
In general, the total amount of DDoS attacks in Q1 2020 has increased as well. During this period, Kaspersky DDoS Protection detected and blocked double the amount of attacks than in Q4 2019, and 80% more in comparison with Q1 2019. The average duration of attacks also grew: in Q1 2020, a DDoS attack lasted 25% longer than in Q1 2019.
“Outage of internet services can be especially challenging for businesses now, because this is often the only way to make goods and services available to their customers. In addition, widespread adoption of remote working opens new vectors for those responsible for carrying out DDoS attacks. Previously most attacks were conducted against the public-facing resources of companies. We now see that DDoS attacks target internal infrastructure elements, for example, corporate VPN gateways or email servers,” comments Alexey Kiselev, business development manager on the Kaspersky DDoS Protection team.
To help organizations protect themselves from DDoS attacks while staff work from home and during significant spikes in attackers’ activity, Kaspersky recommends taking the following measures:
- Do not panic. Unexpected traffic peaks may look like a DDoS attack, but these instances can be caused by legitimate users. They can visit resources which were not as popular before, at times they were not previously accessing them.
- Conduct a fault tolerance analysis of your infrastructure to identify weak nodes and increase their reliability. Attack vectors and traffic peaks are changing, so some resources may work unstably.
- Consider DDoS protection for your non-public services. Their importance to business continuity may increase, making them a target for malefactors.
