Financial malware recorded 1.2 million detections in 2016—more than twice that of ransomware detections—according to Symantec’s 2017 Financial Threats Review released in the Philippines last July 18.
The Trojan Ramnit (W32.Ramnit) alone equaled the total detections of all ransomware combined in the past year. Bebloh (Trojan.Bebloh) and Zeus (Trojan.Zbot) joined Ramnit in the top three financial malware families in 2016, responsible for 86 percent of all global detection; Snifula (Trojan.Snifula) follows in fourth.
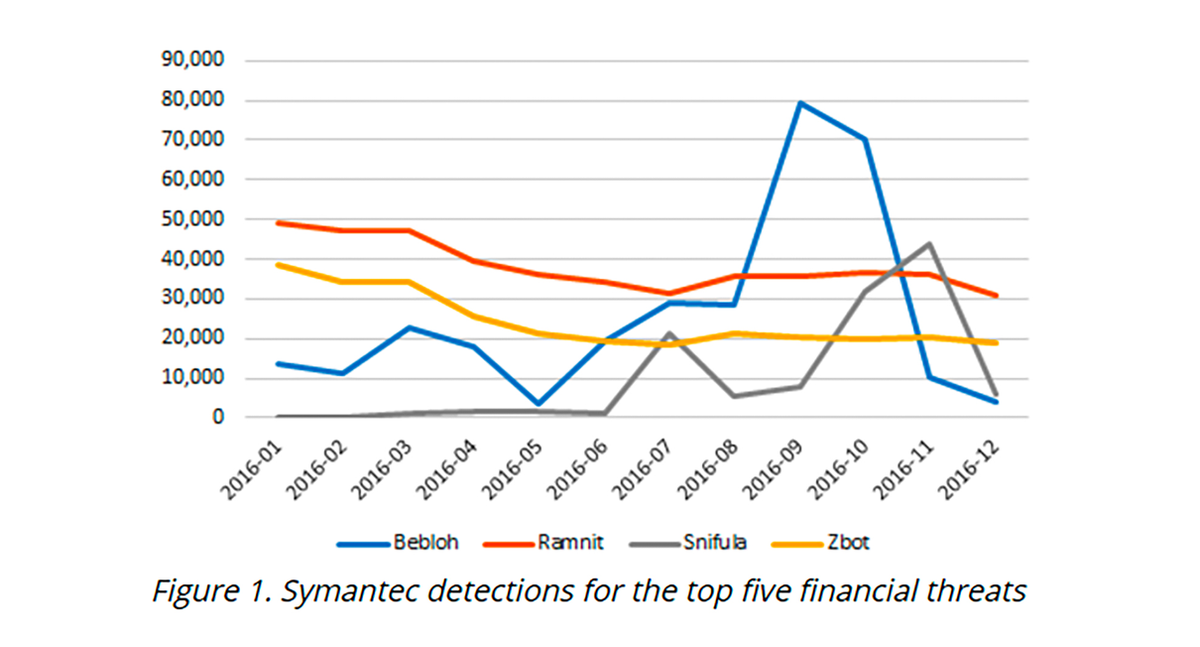
In the second half of 2016, Bebloh and Snifula began focusing on 20 banks in Japan spread through spam e-mails with double extension attachments in the guise of scanned documents. This led to a spike in detections for both Trojans.
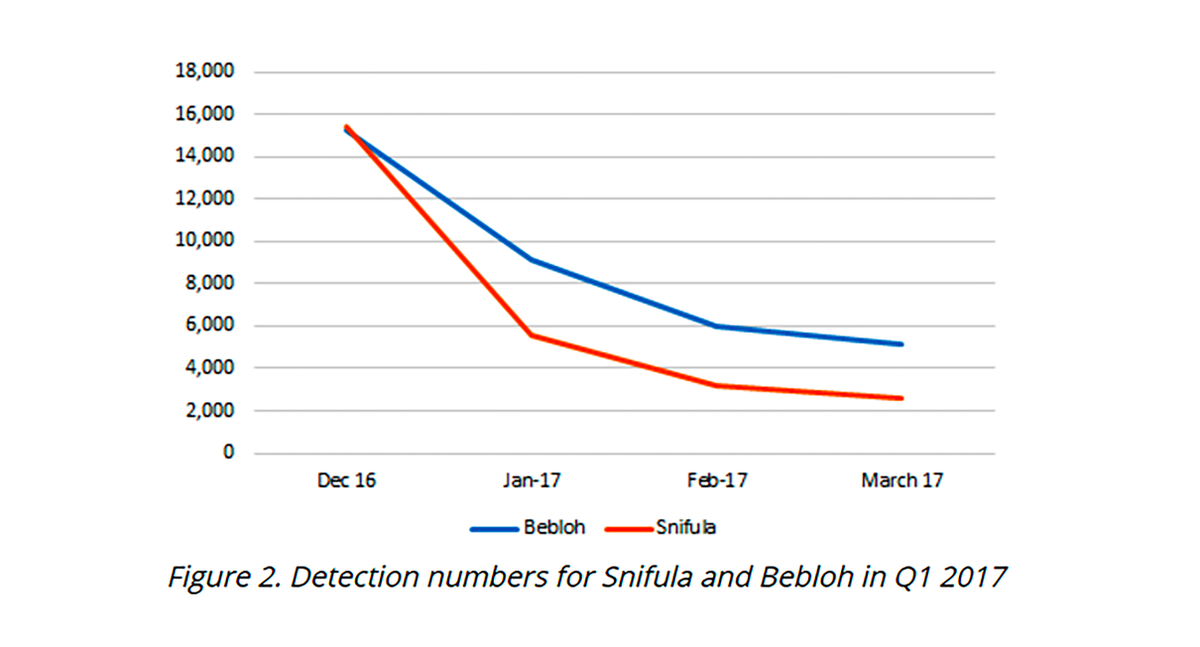
By the start of 2017, however, Bebloh and Snifula activity dropped sharply.
The Avalanche malware-hosting network used by Bebloh was dismantled at the end of 2016, leading to the Trojan’s decline in activity by 66 percent from December 2016 to March 2017.
In January 2017, the arrest of the allaged author of Snifula led to a decrease in its detection by 83 percent in the same period.
While there is a 36 percent decrease in global detection for financial malware in 2016, this has largely been attributed to earlier blocking in the attack chain and a switch by entities to more focused attacks.
Since the attackers target potentially large profits, they have veered towards primarily attacking banks and financial institutions instead of consumers. This trend peaked in 2016, when several high-value heists were executed against institutions connected to the SWIFT network, resulting in millions of dollars lost to cybercrime organizations and nation-state sponsored attackers such as the Lazarus group.
Apart from Trojans and other financial malware, criminals are known to use different points of attack including online banking (phishing, hacking), ATM and POS machines (physical theft), and fraudulent interbank transactions using stolen credentials acquired through social engineering.
Symantec urges the public to be vigilant while offering the people its three-pronged, Prevent-Contain-Respond approach to protection.
Prevention is by far the best case scenario regarding such attacks; adopting a robust defense against common infection vectors such as emails and infected websites will help reduce the risk of infection.
In addition, users should consider the following to reduce the risk of cyber-attacks:
- Exercise caution when conducting online banking sessions, in particular if the behavior or appearance of a bank’s website changes
- Notify financial institutions of any strange behavior while using their services
- Exercise caution when receiving unsolicited, unexpected, or suspicious emails
- Keep security software and operating systems up to date
- Enable advanced account security features, like 2FA and login notification, if available
- Use strong passwords for all accounts
- Always log out of your session when done
- Monitor bank statements regularly
- Be wary of Microsoft Office attachments that prompt users to enable macros
Symantec and Norton products protect against the aforementioned financial Trojans with their various detection engines, such as Advanced Machine Learning, file reputation, and behavior detection. In addition to proactive generic detections, they have the following specific detections in place:
- Bebloh
- Snifula
- Zbot
- Ramnit
- Cridex
- Boyapki.E
